
6 Reasons Why Dexit Stands Out as a Leading Healthcare Document Processing Tool
Managing healthcare documentation is one of the most time-consuming and error-prone tasks in the industry. …
Sensitive patient information privacy and security are paramount concerns of the Health Information Management (HIM) industry. So, one of the primary things that any HIM manager would look for in their healthcare document management software would be an efficient access control feature that would ensure the optimum protection of their Patient Health Information (PHI).
Dexit is a HIPAA-compliant healthcare Document Management System that has been curated by seasoned Healthcare Information Management leaders who have first-hand experience with the existing healthcare document management challenges in the industry. One of the unique features of Dexit is its Role-based Access Controls that provide PHI access to users based on their specific roles. In this blog, we will delve into the nuances of Dexit’s Role-based Access Control feature and how they play an important role in driving Dexit to the forefront of healthcare document management.
Explore:
The healthcare industry faces numerous challenges in securing Protected Health Information (PHI), primarily due to the sensitive nature of patient data and the increasing complexity of healthcare systems.
Embracing the most current healthcare standards, Dexit goes beyond the basics to provide ultimate healthcare data security for health organizations. One of its standout features is the implementation of its Role-based Access Controls, which offer unparalleled flexibility and adaptability in managing system security and user settings.
1. Controlling Access With Precision
Dexit's Role-based Access Controls empower administrators to finely tune user permissions. Whether it's launching the program independently, adjusting various settings, or accessing specific queues and document types, organizations have granular control. This level of precision ensures that only authorized personnel can access and modify critical data, reducing the risk of unauthorized breaches.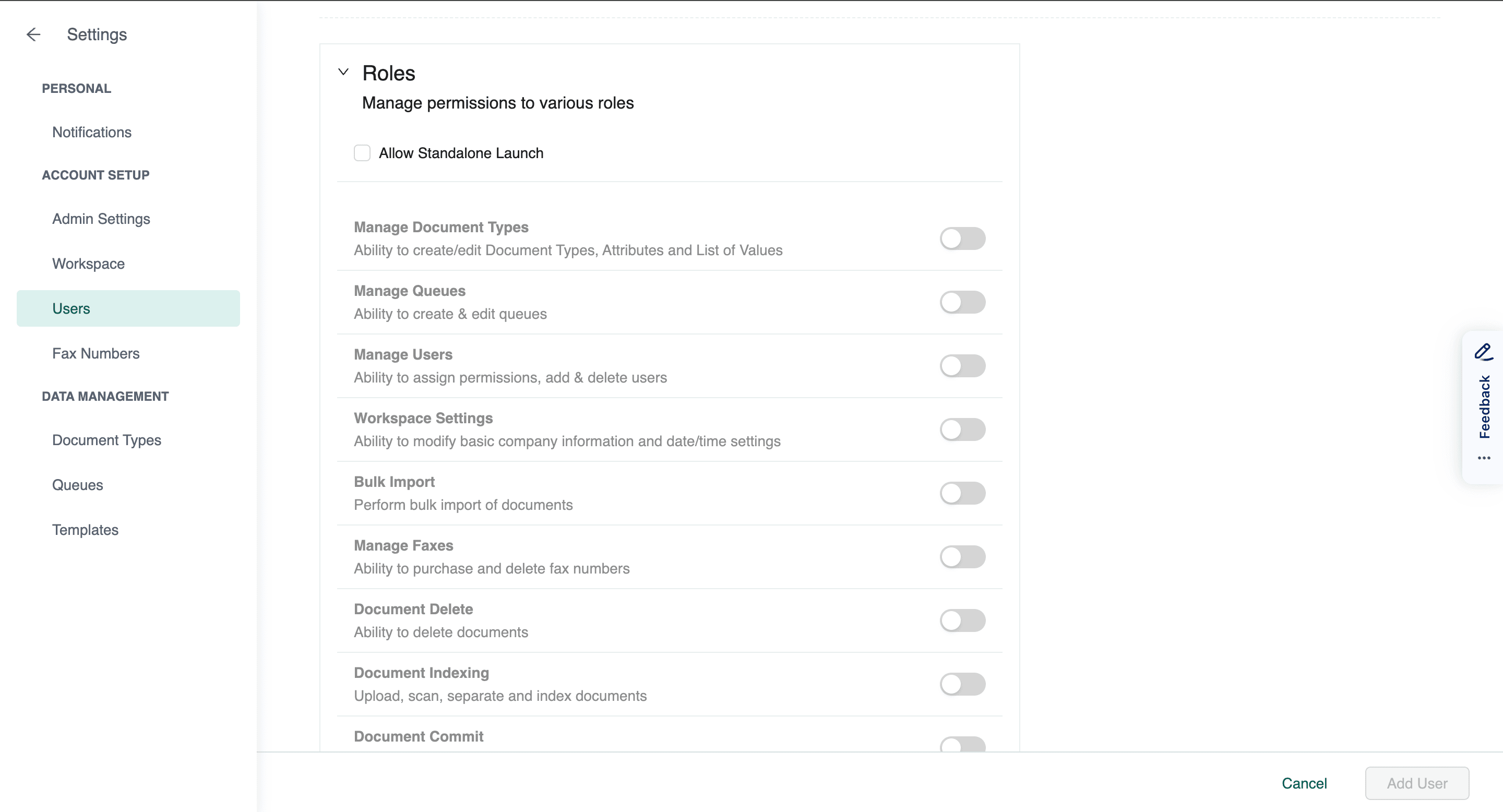
Image 1: Dexit’s RBAC feature allows users to finely tune user permissions
2. Granular Control Over Fax Numbers
In the healthcare sector, even access to specific fax numbers can be a sensitive matter. Dexit allows administrators to exercise control over who has access to specific fax numbers, adding an extra layer of security to sensitive communications.
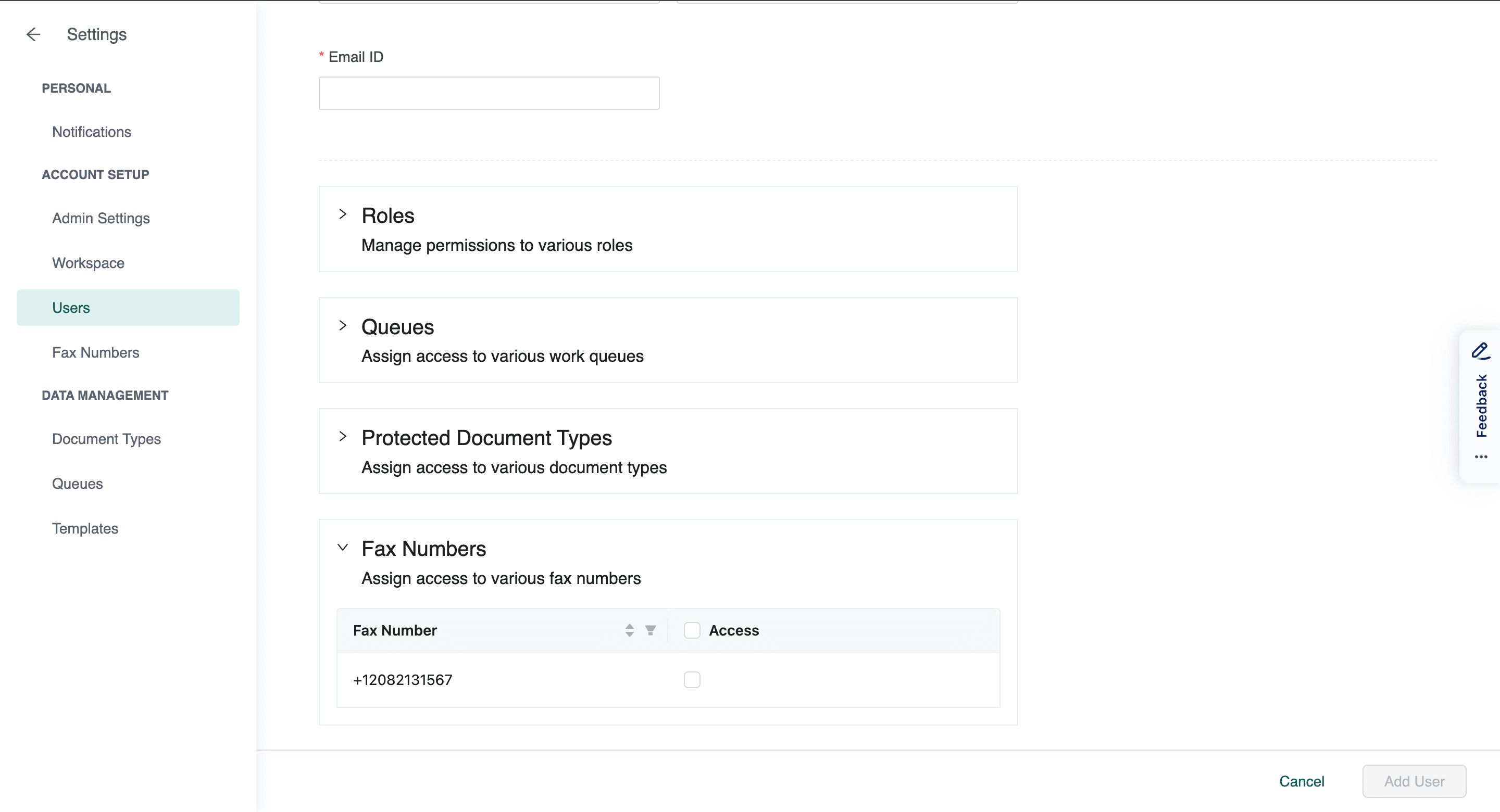
Image 2: Dexit empowers users to have control over who has access to fax numbers
3. Flexibility in Role Definition
The flexibility provided by Dexit extends beyond the organization's boundaries. Administrators can create and define roles for new users, even those external to the organization. This feature streamlines onboarding processes and ensures security measures are maintained even when collaborating with external parties.
4. Localized Security Settings Management
Unlike many integrated enterprise Document Management Systems that centralize control at the vendor level, Dexit empowers organizations with localized control. Client system administrators have direct access to security settings, batch settings, fax settings, and more. This not only expedites organizational changes but also facilitates swift responses to access requests.
5. A Relief From Vendor-level Constraints
Dexit’s approach to security is a breath of fresh air for organizations that have historically grappled with vendor-level constraints. Many integrated enterprise Document Management Systems impose controls at the vendor level, leading to compromises in established workflows and unnecessary delays. Dexit's localized approach ensures that organizations can tailor security measures to fit their unique needs without sacrificing efficiency.
Join over 3,200 subscribers and keep up-to-date with the latest innovations & best practices in Healthcare IT.

Managing healthcare documentation is one of the most time-consuming and error-prone tasks in the industry. …
In the ever-evolving healthcare landscape, the efficient management and secure exchange of patient information …
The advent of Artificial Intelligence (AI) has signaled a revolutionary shift across various sectors, with the …