EHR Data Transformation: The Overview You Need
As the healthcare IT landscape evolves, the importance of EHR applications grows significantly. Therefore, …
Digitization has revolutionized our every day, and while it is true that it has improved efficiency, it is also important to note that it has brought in a handful of challenges that require immediate attention. A data breach is one such challenge that we need to deal with. A data breach refers to any situation where the safety of the data is compromised. Any of the following cases, like accessing, stealing, and transmitting confidential data, could be considered a data breach. Data breaches in healthcare have shot up to quite an extent; a cybersecurity report identified a 35% increase in attacks on health plans in 2021. The immense value of healthcare data makes it prone to such breaches. Health data is considered valuable because it possesses an individual’s personally identifiable information.
Continue reading this article to know more about:
As per the data breaches reported to the U.S. Department of Health and Human Services (HHS), 45 million individuals were affected by healthcare data attacks in 2021. The following are some of the causes that contribute to the increasing number of data breach cases in healthcare:
In most cases, healthcare data breaches mainly occur because of negligence or unintentional actions that cause harm. Those in charge of handling health data err at times due to the increased burden of handling many tasks. Some of the most common errors that cause data breaches are misdelivery or health data being sent to the wrong person, improper disposal of patient records, and loss of health data.
The next major cause is the case of data being misused and accessed by an unauthorized person. The most common case of misuse of health data would be on the part of third-party vendors who have access to the VPN or other shared credentials. Most hackers use emails as a medium to attack through a third-party’s network access and gain access to patients’ Electronic Protected Health Information (ePHI). Also, it is important to note that once hackers get access to a VPN, there is no way of restricting permission, and they have unlimited access to loads of patient data.
Whenever healthcare organizations switch from one system, application, or device to another, they usually migrate most of the health data and dispose of some of it. Therefore, when discarding ePHI, it is important to remember that just deleting the sensitive data from the hard drive won’t work. Data deleted from the hard drive would still exist in sectors of the memory in which it was originally contained until there is overwriting. Even with Solid State Drives (SSDs), there are ways to recover deleted data. Hence, it is important to ensure that whatever ePHI is disposed of must be done by following an irreversible procedure. Another problem with improper disposal is that it could lead to your healthcare organization falling under the realm of HIPAA violations.
Healthcare is definitely not new to the world of data breaches. According to HIPPA Journal, there have been about 4,419 healthcare data breaches of 500 or more records between the years 2009 and 2021. Here are some healthcare data breaches from the HIPAA Journal that offer us lessons to learn.
The Breach: The exploitation of the vulnerabilities of the firewall vendor - Accellion File Transfer Appliance (FTA), affected the data of 11 healthcare organizations in the U.S.
Data compromised: Protected Health Information (PHI) of at least 3.51 million individuals.
Learnings: Always assess the internal risks that could pave the way for data breaches.
The Breach: The Florida health plan data was hacked as the security vendor failed to apply security patches to fix vulnerabilities on the Florida Healthy Kids Corporation’s website.
Data compromised: Social Security Number (SSN) and financial information of 3.5 million individuals.
Learnings: Always keep a check on the data protection measures taken by your security vendor.
The Breach: Unauthorized access to personal and health data as the Amazon Web Services S3 cloud storage bucket was misconfigured.
Data compromised: SSN, Date of Birth (DOB), and health insurance information of about 3,253,822 individuals. Learnings: Always keep track of how the services of your third-party vendor are performing and see that it is meeting set standards.
It is always best to begin internally and determine the risks in your healthcare organization. A risk assessment could be done to see how well the organization is meeting the security needs of protecting ePHI. The HIPAA Security Rule is a guiding standard that could help you assess risks, improve security measures, and become HIPAA compliant.
The third-party service providers that you tie up with for services like data archival, migration, medical billing, app rationalization, etc., could impact the safety of your data. So make sure to partner with experienced vendors and always check their security policy.
For each data set in your healthcare organization, decide who would have access to it. Have a standard policy that states the rules for data accessibility and ensures restricted access to sensitive data while keeping the information blocking requirements and guidelines in mind.
In healthcare, it has been observed that personal devices are used mainly to ensure quick remote access. Attempt to limit the use of personal devices by having a clear policy that states what personal devices can be connected to the internal network and what cannot.
When it comes to security, it is important for your healthcare staff to be fully aware of the security needs and the ways to meet them. This is only possible when they are continuously trained to meet their needs. Ensure the education and training enable them to be aware of and meet HIPAA requirements.
Even if your healthcare organization is meeting all the HIPAA requirements and has a strong data security policy, it is always good to be prepared to meet uncertainties. An incident response plan could help you act quickly in the hour of need and minimize damages.
Outdated infrastructure can increase the data security risks. Follow regular health IT upgrade procedures for outdated devices. Upgrading the infrastructure could also help you meet the compliance requirements in a better way.
When it comes to vendor partnerships, always review service-level agreements with your vendors. Check the terms and conditions of the agreement and see that your organization holds ownership rights over the data.
The importance of having a secured disposal procedure for ePHI cannot be stressed enough. The help of certified service providers could also be taken to ensure proper procedure for destroying data.
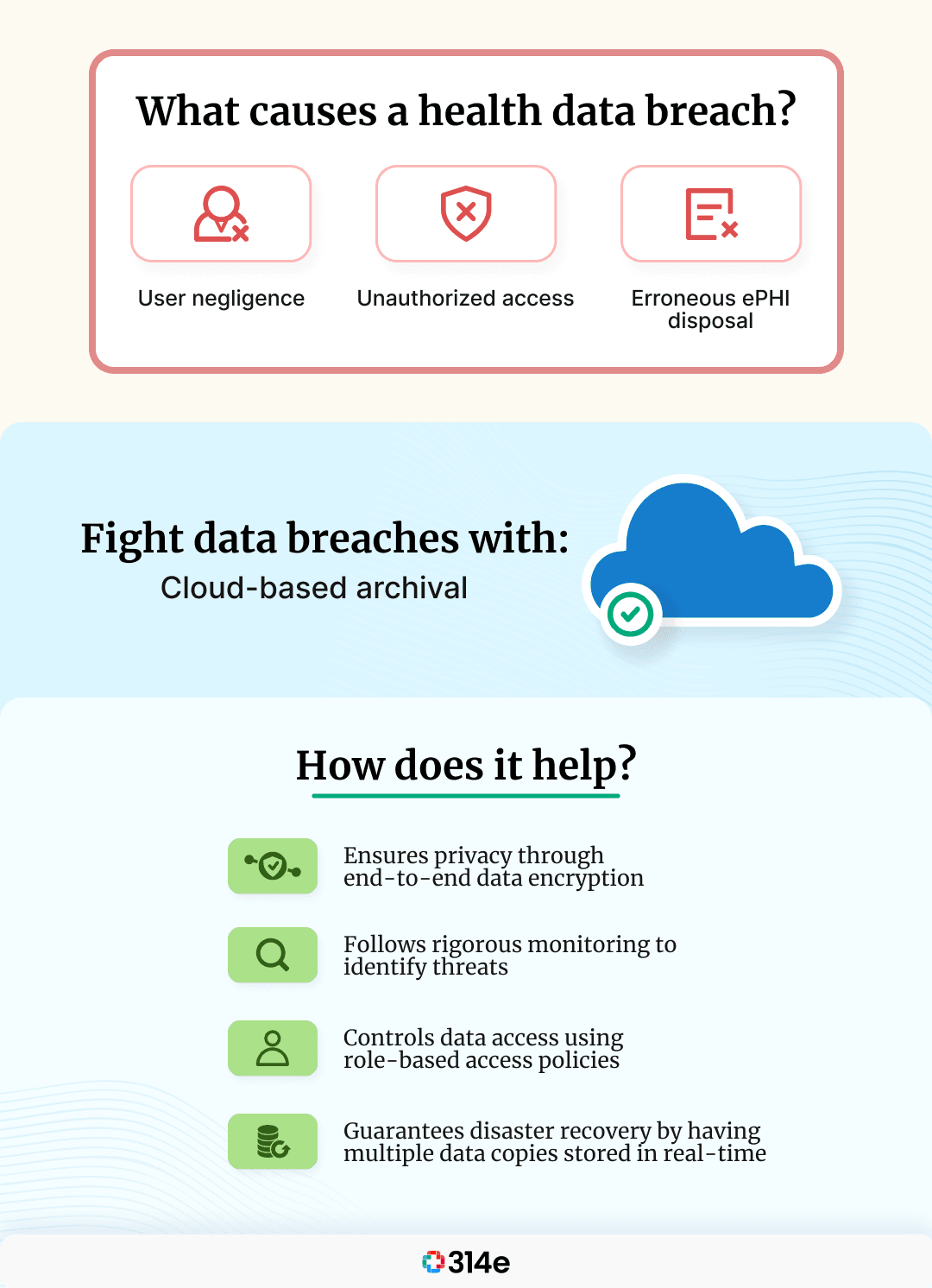
Cloud-based archival could be an effective tool that could help you stay from the terror of data breaches.
A cloud-based archival software refers to storage as a service that offers an independent repository for critical data to be stored. The critical data stored on a cloud archival platform is secure and tamper-proof. Data archival can also help you take control of the governance policies that decide the data access, transfer, and disposal.
Muspell Archive is an intelligent cloud-based archival platform that doesn’t lock data away but unlocks the value of data. Be it archiving clinical data or non-EHR data; it is the one archive that meets all your needs. It has intelligence built in to meet the requirements of discovery, data delivery, migration, and security.
Muspell Archive minimizes the risk of data breaches by:
The increased importance of health data protection has caused the need for healthcare organizations to partner with vendors that provide intelligent solutions to ease the burden of data maintenance and security. This calls for healthcare organizations to be extra careful when choosing their data security vendor, as this decision can make or break their organization’s health data security.
Join over 3,200 subscribers and keep up-to-date with the latest innovations & best practices in Healthcare IT.

As the healthcare IT landscape evolves, the importance of EHR applications grows significantly. Therefore, …

An authorization for Release of Information form (ROI) allows your patients to specify which parts of their …
The challenges associated with connecting multiple, disparate EHR systems — be it ancillary provider or …